New PhishPoint Attack May Be Affecting As Many As 10% of Office 365 Users
Recently we have been seeing a new phishing attack called PhishPoint that is targeting Office 365 customers. In this scam, cybercriminals are inserting malicious links into SharePoint files and then sharing them with potential victims, ultimately allowing them to steal Office 365 user credentials.
This attack is particularly insidious because it bypasses Office 365’s built-in security. Microsoft automatically scans incoming emails for malicious links and attachments, but a link to Microsoft’s own SharePoint Online platform wouldn’t raise any red flags with their system. Because the malicious phishing link is hosted in the SharePoint file rather than the email itself, is goes unnoticed by Microsoft’s email security.
How to Spot A PhishPoint Attack
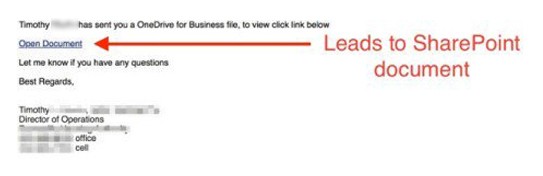
In a PhishPoint attack, the target will receive an email that looks exactly like the standard SharePoint invitation to collaborate:
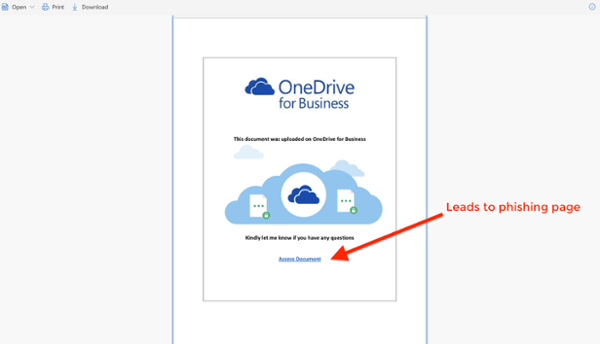
Clicking on the link will automatically open up a SharePoint file. This SharePoint file will contain content that looks like a standard request to access a OneDrive file. However, the link to “Access Document” is actually a malicious URL.
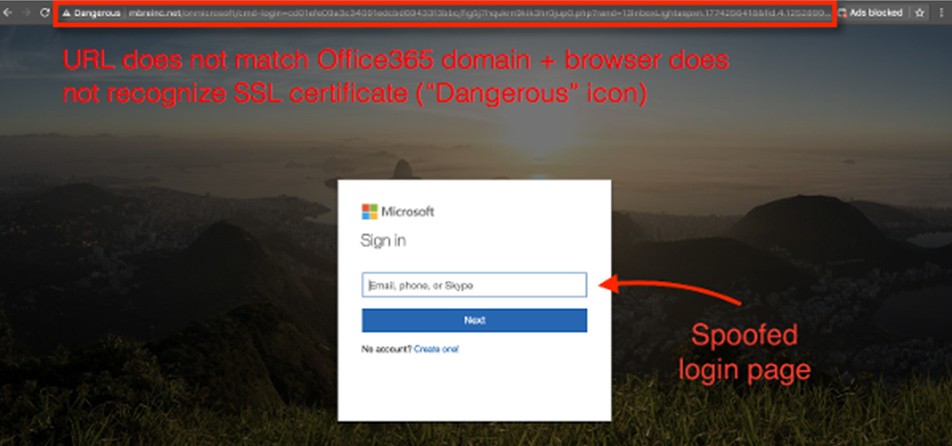
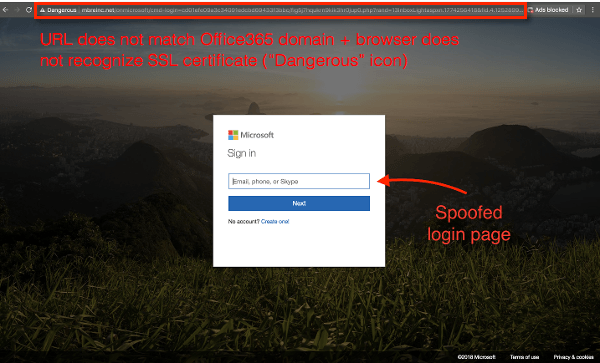
Clicking on the SharePoint link to access the document takes the user to a spoofed Office 365 login page. When the victim enters their username and password, their credentials will be recorded and stolen by the hacker.
How Can You Protect Yourself?
Like many phishing attacks, PhishPoint is designed to perfectly imitate aspects of the Office 365 experience in order to lull users into a false sense of security. Here are a few things to keep in mind:
- PhishPoint emails are unsolicited and usually have a generic subject line like “[fusion_builder_container hundred_percent=”yes” overflow=”visible”][fusion_builder_row][fusion_builder_column type=”1_1″ background_position=”left top” background_color=”” border_size=”” border_color=”” border_style=”solid” spacing=”yes” background_image=”” background_repeat=”no-repeat” padding=”” margin_top=”0px” margin_bottom=”0px” class=”” id=”” animation_type=”” animation_speed=”0.3″ animation_direction=”left” hide_on_mobile=”no” center_content=”no” min_height=”none”][name] has sent you a OneDrive for Business file”. If you are not expecting a file share from someone in your office, take the time to verify the email’s legitimacy by calling the sender directly or, better yet, talking to them in person.
- Many PhishPoint emails attempt to manufacture a sense of urgency by including words like ACTION REQUIRED or URGENT in their subject lines. Don’t let the sense of urgency put you in a hurry—take the time to look closely at emails like this before clicking on them.
- Always check the URL when you receive suspicious links! In PhishPoint’s case, when you finally make it to the login page, you can tell that it is not associated with the Office 365 domain by looking at the address bar in your browser.
To learn more about how to spot phishing attacks, check out this helpful video. As always, make sure you stay alert and think before you click![/fusion_builder_column][/fusion_builder_row][/fusion_builder_container]