Top 3 IT Priorities for 2022

2021 has been another year of “unprecedented times” as the COVID-19 pandemic has continued long past what many expected. With this continued level of uncertainty, it’s more important than ever that organizations have their IT in order and prioritized. Our team here at TechMD have put together three top IT priorities for 2022 to help you be prepared for the ever-changing IT landscape.
Help Your Team Get Things Done with Microsoft Planner

Microsoft 365 comes with a suite of productivity tools that seamlessly integrate with one another, allowing organizations to manage their workflow, communications, and storage all in one place. Microsoft Planner is Microsoft’s task management tool that makes it easy for teams to collaborate and organize their work visually.
Communicate Better with Microsoft Stream

Internal communications can be a headache—we’ve all received emails that were longer than they needed to be, and many of us have probably sent long emails that never got read. But there’s a better way: start sending short videos instead of long emails with a tool like Microsoft Stream.
Zero-Day Exploit Affects Microsoft Exchange Servers

Microsoft has announced that Hafnium, a Chinese-backed cybercriminal organization, has been taking advantage of four zero-day exploits to attack on-premises Microsoft Exchange servers. We strongly recommend that any organizations with on-premises Exchange servers, including hybrid Office 365 setups, should apply Microsoft’s patch immediately.
Top 3 IT Priorities for 2021

2020 was an unprecedented year, and businesses with inflexible IT solutions had a rough time during the pandemic. And with continuing uncertainty, most organizations we talk to are trying to avoid getting surprised by sudden IT issues and costs over the upcoming year. Here are three key priorities to make sure your business isn’t caught off guard by IT in 2021.
Top 5 Cloud Trends for SMBs in 2020

The coronavirus pandemic has drastically accelerated the pace of cloud adoption, as organizations nationwide were forced to migrate to a fully remote workforce in a matter of days. Even as many organizations return to the office, remote work and cloud infrastructure is here to stay. Here are our top 5 cloud trends for small and medium businesses.
5 Ways to Conserve Cash by Reducing IT Spend
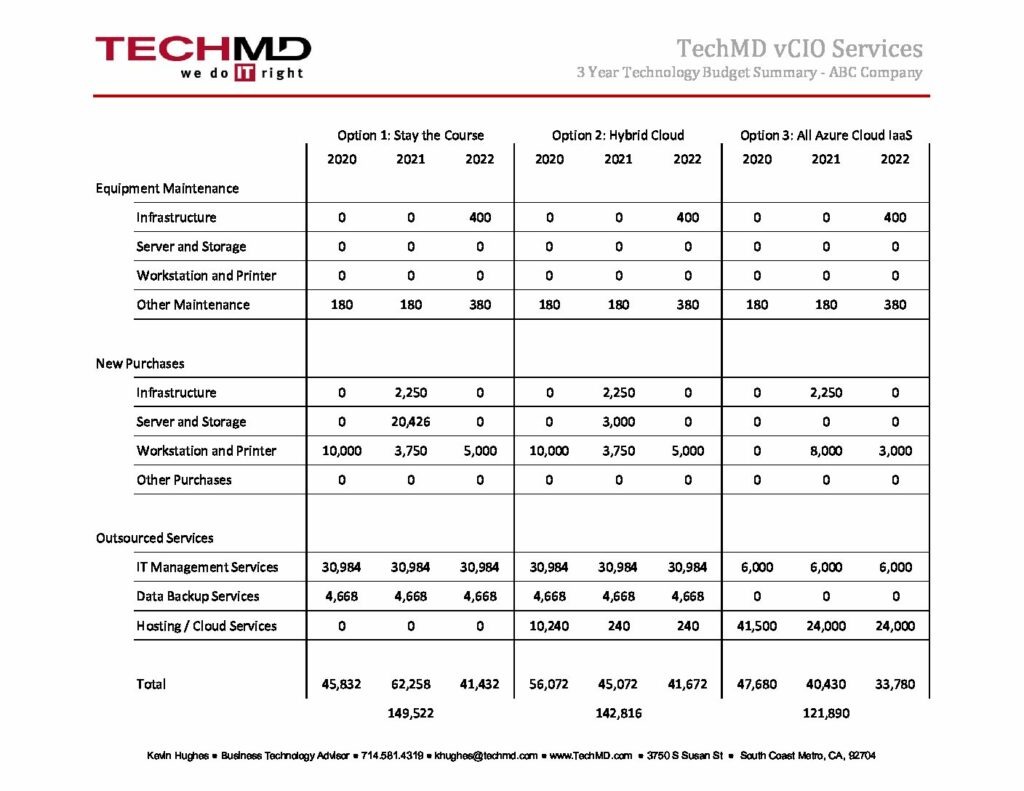
While we anticipate the re-opening of the economy, most organizations across the country are still working through tough decisions about how to best conserve cash. Because IT spending is normally a significant line item, finding smart ways to reduce it can make a big difference in improving cash flow.
Are all your IT eggs in one basket?

Can you evaluate risk with your organization’s information technology (IT)? Unfortunately, many businesses that we speak with on a regular basis do not realize they are one unexpected circumstance away from a business disaster.
Does the new CCPA law apply to your business?
Many California businesses will need to address new compliance and privacy requirements this year due to the California Consumer Privacy Act (CCPA), which went into effect on January 1st, 2020. Does CCPA apply to you, and if so, what do you need to do about it?
Tech Talk: How to Develop an IT Strategy for the Coming Year

With the new year approaching, it’s time to start thinking about how your technology will move your business forward in the coming years. On this episode of Tech Talks, Sebastian Igreti discusses 5 important steps you should consider while planning your IT strategy for the coming year.
Tech Talk: Windows 7 End of Life

In January 2020, Microsoft will cease support for Windows 7, along with a few other programs. This means that your organization may need to make some upgrades in order to stay secure. Tune in as CEO Sebastian Igreti walks you through the steps you need to take to prepare for the changes in Windows 7.
Tech Talk: Is AI Ready For Small Business?

AI is an emerging technology surrounded by lots of news and speculation. But is it a technology that your small business currently needs? On this episode of Tech Talks, Sebastian Igreti discusses whether AI in its current form makes sense for small and medium businesses, and touches on a few AI tools that you may be able to leverage today.
Cybersecurity Alert: SharePoint Phishing Attack Targets Office 365 Users
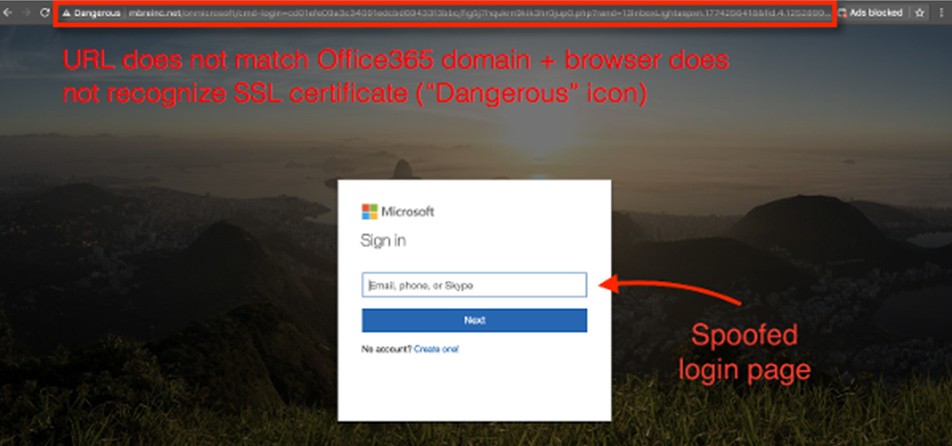
Recently we have been seeing a new phishing attack called PhishPoint that is targeting Office 365 customers. In this scam, cybercriminals are inserting malicious links into SharePoint files and then sharing them with potential victims, ultimately allowing them to steal Office 365 user credentials.
Tech Talk: Work Seamlessly with Office 365

Microsoft Office 365 includes a wide range of cloud applications that can revolutionize productivity, collaboration, and work mobility. In this Tech Talk, Sebastian Igreti tours Office 365 and discusses how it can transform the way businesses leverage the traditional Office software stack.
Tech Talk: Microsoft Azure VDI: A Game Changer

Microsoft recently announced their Azure Virtual Desktop Solution, which allows organizations to move their entire IT infrastructure into Microsoft’s first-class cloud environment. If you’re interested in learning more about what’s on the IT horizon and how it can benefit your organization, check out this episode of Tech Talks, where Sebastian Igreti discusses the latest in cloud technology.
Cloudflare Announces Possible Breach of User Credentials

Make sure you change duplicate passwords immediately! On Thursday of last week, website security provider Cloudflare announced a major security vulnerability affecting their service. This vulnerability has caused sensitive user data to be exposed across a number of popular websites, like Yelp, Uber, and others. To protect yourself, make sure you are not reusing any […]
