How Does the FTC’s Amended Safeguards Rule Affect Your Business?

Safeguarding sensitive information is critical for businesses entrusted with handling customer data. In October 2023, the Federal Trade Commission (FTC) made significant amendments to its Safeguards Rule, introducing mandatory data breach reporting and specific reporting requirements. While the rule primarily affects non-banking financial institutions such as mortgage brokers, motor vehicle dealers, and payday lenders, the […]
AI Tools for Productivity at Work

AI tools for productivity at work, such as ChatGPT, Copilot, and other AI software, can do so much more than what you’re probably using them for. In this episode of Cup of IT, join TechMD Chief Strategy Officer David Bryden in conversation with Sebastian Igreti, as David reveals the innovative ways he’s leveraging AI tools […]
TechMD Recognized as a Pioneer 250 Managed Service Provider by CRN

We are proud to announce our inclusion in CRN’s Managed Service Provider (MSP) 500 list for 2024, under the Pioneer 250 category, an honor we’ve received for the ninth time in a decade. This accolade reaffirms TechMD’s position as a leader in the managed services sector where we continue to pioneer innovative solutions that enhance operational efficiency, simplify IT, and maximize return on investment for our clients.
TechMD Named One of the Top Workplaces in Orange County by the OC Register

TechMD is thrilled to announce its inclusion in the prestigious Top Workplaces list by the Orange County Register. This recognition highlights TechMD as one of the top employers in Orange County due to its commitment to fostering a positive and empowering workplace culture.
TechMD Featured as a Top Partner at Microsoft Inspire 2023

Recognized for workplace modernization for SMB Microsoft Inspire 2023, held on July 18th and 19th, brought together 400,000 Microsoft partners for a celebration of outstanding achievements impacting businesses and industries worldwide. The global event featured Microsoft’s annual Partner of the Year Awards (POTYA), which acknowledge outstanding successes by partners who utilize Microsoft technologies to provide […]
ICS Changing Name to TechMD

ICS, a technology management, and cybersecurity company headquartered in Endicott, NY announced today that they will consolidate their regional Managed Technology brands into one national brand, TechMD. ICS, founded in 1987, was purchased by partners, Kevin Blake and Travis Hayes in 1995. After several recent acquisitions including AKUITY Technologies, Cards Technology, and TechMD, ICS will roll […]
ICS Ranks Again on Channel Futures 2023 MSP 501 List — Moving Up 276 Spots From 2022

We are so proud and honored that ICS (now TechMD) has achieved a remarkable milestone by securing the 160th position on the prestigious 2023 Channel Futures MSP 501 list, moving up an impressive 276 places from last year’s ranking, demonstrating our relentless pursuit of excellence. ICS gained an envious position on this list due to our […]
ICS Completes SOC 2 Type II Certification

ICS (now TechMD) understands the value of our client’s data to their reputation and future success. Because of this, ICS is proud to announce that it has achieved Service Organization Control (SOC) 2 Type II certification standard. SOC 2 compliance helps provide cybersecurity assurances to professional services firms and other companies that are working with […]
ICS Named as a Pioneer 250 Managed Service Provider by CRN

We are so honored to be named, once again, as CRN’s Managed Service Provider (MSP) 500 list in the Pioneer 250 category for 2023. MSP 500 list identifies the industry-leading service providers in North America who are driving a new wave of growth and innovation for the channel through forward-thinking approaches to managed services, helping end users […]
TechMD Announced as a 2022 National and Local Excellence Award Winner by UpCity!

We are proud to announce that TechMD has been recognized by UpCity, not only as one of the best B2B service providers of 2022 in Los Angeles and Orange County, but also as one of the top B2B providers in the United States!
TechMD Named on UpCity’s 2021 Local Excellence Awards!

We are excited to announce that TechMD has been recognized as one of the top B2B service providers of 2021 by UpCity! Each year, UpCity analyzes and scores more than 70,000 service providers based on their Recommendability Rating and acknowledges the top national and local providers with an UpCity Excellence Award.
TechMD is SSAE-19 Certified!

TechMD is proud to announce that we are now certified as operating under the Statement on Standards for Attestation Engagements (SSAE) No. 19, based on the Center for Internet Security’s (CIS) Critical Security Controls. We are one of the first Managed Service Providers in Southern California to have received this certification.
TechMD Named Best Managed IT Service Provider of 2020 by Digital.com

We are proud to announce that Digital.com, a leading independent review website for small business online tools, products, and services, has named TechMD to its list of best managed IT service providers of 2020!
TechMD is a 5-Star IT Solutions Firm!
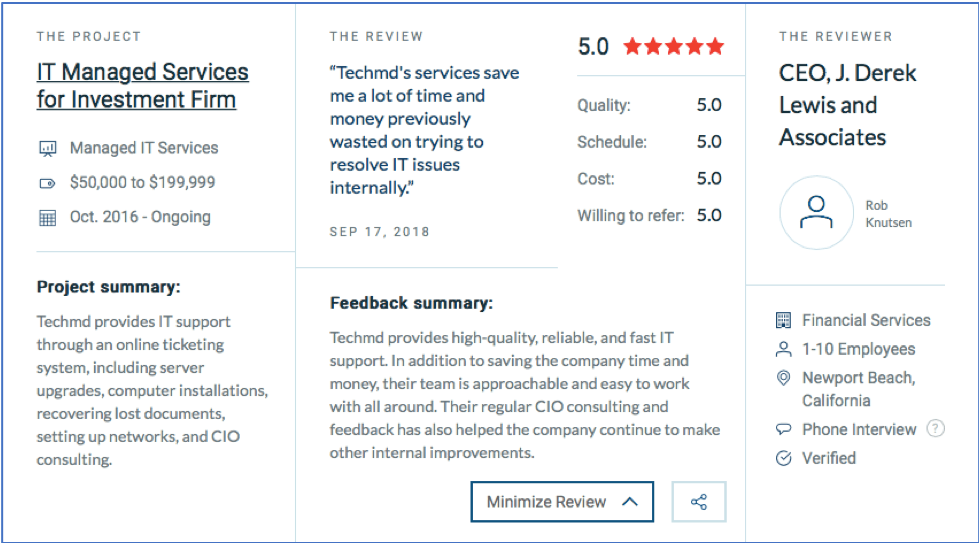
We succeed when our clients succeed, and there’s nothing we appreciate more than hearing our client’s success stories. Recently we received a 5-star review from PROMOFILL, a third-party logistics company that focuses on e-commerce, fulfillment, and multi-chain distribution.
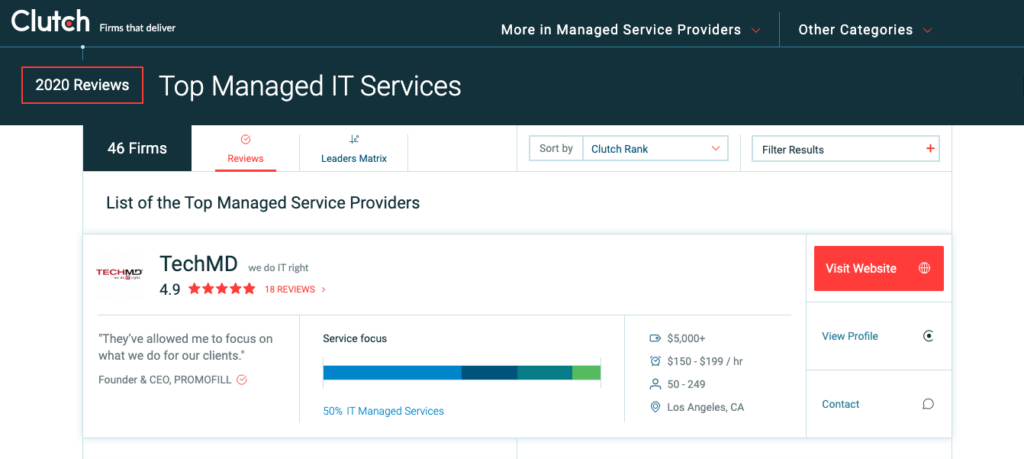
Clutch Selects TechMD as #1 IT Services Firm in L.A.
TechMD has been selected by Clutch as the #1 IT Services firm in Los Angeles for 2019. A B2B ratings and reviews site, Clutch compiles and publishes updated reports on the top performing companies on the platform. TechMD is # 1 out of the 30 companies that were selected as leaders in this category!
OC Register Honors TechMD on Top Workplaces 2018

Every year the Orange County Register compiles their list of the top workplaces in Orange County, and TechMD placed #16th in the small businesses category for Top Workplaces 2018. We are proud to have been included on this list for the fourth year in a row! At TechMD, we are passionate about investing in our […]
