Most cybersecurity assessments today do not follow an authoritative framework, are incredibly expensive for what they provide, and (most importantly) fail to answer these three critical questions:
- How secure is our business today?
- What is the appropriate level of cybersecurity for our business?
- How can we improve cybersecurity practices to meet business objectives?
TechMD’s Security Maturity Level Assessment (SMLA) process fully answers these three questions by following the nationally-recognized NIST Cybersecurity Framework (you can learn more about NIST framework here). And with an all-in flat-rate price of $6,000 for the entire SMLA process, our assessment is as cost-effective as we can make it.
Here is an overview of how TechMD conducts the NIST SMLA and what we provide once we’re finished:
Security Maturity Level Assessment (SMLA)
Step 1: Confirmation of Business Cybersecurity Requirements
The SMLA process begins with scheduling a complimentary meeting where TechMD will seek to understand your business cybersecurity needs, what your cybersecurity posture looks like today, and how your IT infrastructure, IT systems, and IT support are set up. By the end of this meeting, you’ll understand how the SMLA process works, you’ll know the all-in flat rate costs for the assessment, and you’ll have a high-level overview of how our process will impact your overall cybersecurity posture.
If you want to move forward, we’ll sign an SMLA agreement and will begin the process of identifying the key personnel that will need to be interviewed as a part of the assessment process. Click here for a sample Statement of Work document for the SMLA.
Step 2: Interviews with Key Personnel
The SMLA is built to follow the NIST Cybersecurity Framework and the CIS Top 20 Cybersecurity Controls. Once we begin the assessment, we will sit down with key personnel, usually a C-level executive plus whomever manages IT and HR, to understand how your organization stacks up against the NIST framework and CIS Top 20 Controls.

This is a highly-detailed, structured process where we assess the status of and execution on each of the CIS 20 controls and sub-controls one-by-one. The goal is to understand whether there is a policy or practice in place that satisfies each control, and if so, to what extent it satisfies the control. For each control, we’ll be looking for:
- Is there a verbal policy that satisfies this control?
- If yes, is there a written policy that satisfies this control?
- If yes, is the policy fully automated?
- If yes, is there a reporting process in case the policy fails to execute properly?
Once we gather all the data for each of the CIS 20 Controls, we will make evidence requests to prove compliance. We will also be documenting everything along the way and maintaining an inventory of evidence provided. This is important because we are taking the position of an outside auditor—our job is to ensure that you can pass an independent audit, and we will stand behind you if and when you decide to engage one.
Step 3: Review the Evidence
Once the initial key personnel interviews and evidence-gathering process is completed, we will review the policies provided by the client and the technical evidence provided by the IT team, determine if each policy satisfies its corresponding control and would pass an audit, and finally analyze all the information to get a high-level overview of the organization’s cybersecurity compliance.
After our analysis is complete, we normally expect to schedule follow-up meetings with key personnel to fill in any gaps in information. Once we have a complete picture, we’ll move on to the deliverables.
SMLA Deliverables
As a result of the SMLA process, you will receive:
Official Security Maturity Level (SML) Score
Your SML score will range from 0-5 and will include a full breakdown of the percentage to which each control has been satisfied, along with a comparison to other companies in your industry.
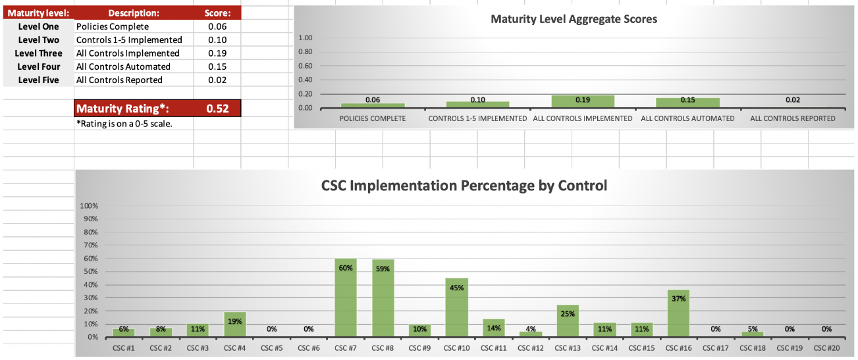
Executive Summary Report
This report contains high-level insights into how your cybersecurity policies fit together and an overview of your overall cybersecurity posture. This report is based on your cybersecurity goals and where you’re falling short in relation to those goals. Not every organization needs to have an SML Score of 4 or 5, so the analysis in this report will be highly dependent on your specific needs and goals.
Full Detail and Risk Analysis Report
This report includes a full breakdown of what is missing from each policy and what is needed to satisfy its corresponding CIS Control, along with an assessment of how much risk each policy presents to the organization.
Customized System Security Plan
The first three deliverables may paint a depressing picture about your cybersecurity posture, and if so, you probably already knew roughly how bad it was. But what you probably want to know is what you should do next, so the most important piece of the SMLA process is the customized System Security Plan (SSP) and its companion Timeline and Budget.
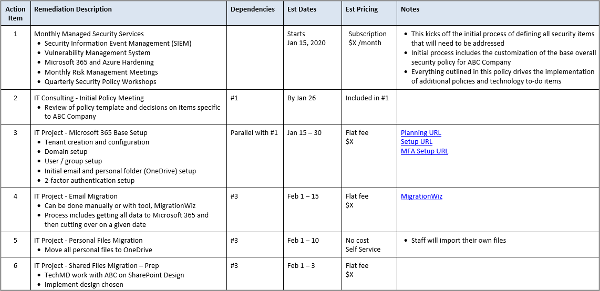
The custom SSP will provide you with a step-by-step plan and budget for improving your SML score. This plan will be designed to satisfy your organization’s specific timeline, budget, and goals—normally we develop 1-year plans, but you may be willing or required to spend more and arrive at your targeted SML score sooner. Our SSP applies to any industry or compliance requirement and will be customized to fit your organization’s needs. For example:
- You may need to be HIPAA compliant, CMMC certified, or follow any number of other industry-specific compliance requirements
- You may need to meet the cybersecurity requirements of a large customer
Once you receive your customized SSP, you’ll have the freedom to execute the plan yourself if you have in-house cybersecurity expertise, or we can help you drive that process forward through a Managed Security Services Agreement.
Get Started Today
It’s easy to get overwhelmed by all the different cybersecurity solutions out there, but it doesn’t have to be that way. We now have a nationally-recognized cybersecurity standard in the NIST Cybersecurity Framework and CIS Top 20 Controls. With the SMLA process built on that standard, TechMD can help you understand your cybersecurity risks and develop a customized action plan that will get you where you need to be, at your own pace and according to your budget.
To learn more about the SMLA, contact us here!




